Simplifying software security
Automate software security testing with AI-powered assistance
Interactive demo
Discover the feel of our product
Who are we?
Unique selling proposition
ScourNomad provides automated software security testing services to software developers and vendors. In essence:
- We automate security testing procedures, both generic and custom-tailored to clients' needs. Our sophisticated artificial intelligence assistant guides our clients while handling day-to-day tasks, reducing the time to completion
- The automated process and the fact that the customers can ask a digital assistant for help 24/7 results in a cheaper and faster alternative than a traditional pentest
ScourNomad provides automated software security testing services to simplify and expedite testing processes and procedures. In essence:
- We provide ready-made testing workflows and procedures to use out-of-the-box, as well as the capabilities to tweak them and create custom ones using an easy-to-use interface
- The workflows use different integrated industry-standard testing tools, for which we provide automatic updates, so your procedures will always be up-to-date
- You can leverage our Artificial Intelligence Assistant during your day-to-day use to help you with your tasks to finish your assignments quickly
The problem: As contemporary software becomes increasingly sophisticated, the developers creating it need to stay up-to-date with the latest software development technologies. This means the developers often focus on development self-improvement rather than software security skillset.
Our solution: ScourNomad provides ready-made tests covering a wide range of software products that can be tested out-of-the-box while also providing utilities to extensively tweak the existing tests or create new ones from scratch - if the existing ones are not up to par. To help with this process, our digital intelligent assistant is always available to our clients to answer any questions and even directly solve the given problems, like auto-fixing security issues or changing the scan procedures according to written specifications.
Get our pitch deck here.
ScourNomad is a DAST tool that can use out-of-the-box workflows and create tailor-made ones from scratch. It also employs an AI LLM, a digital assistant who solves instructed problems and answers questions. The tool provides POCs and confirmations when applicable for easier triage.
-
LLM - Large Language Model
-
POC - Proof of concept, a small program (exploit) as proof of vulnerability impact
Our Impact
Why teams trust ScourNomad
AI Assistant: Datasets
Our AI assistant is fine-tuned using the relevant software security and best development practices datasets, thus making it an ideal competent partner for fixing security issues in different codebases
CWEs covered
Our scanners can scan and detect many different CWEs (classes of vulnerabilities) without user assistance
CVEs covered
The templates in our scans cover scanning a large set of specific CVEs (specific well-known vulnerabilities)
Automation workflows
Our customers can choose from a plethora of workflows to accomplish different tasks. Workflow setup is mostly minimal as they usually pull the required information to perform their functions independently.
Our Solution
Added Value
Improved effectiveness
Risk management
Integrations
Appsec reputation
Insights
AI agent
Vulnerability management
Organizational knowledge management
Integrations
Automated triage
Compliance
AI agent
CI/CD integration
Immediate feedback
Integrations
Actionable reporting
Bugfix automation
AI agent
Product Gallery
See ScourNomad in action
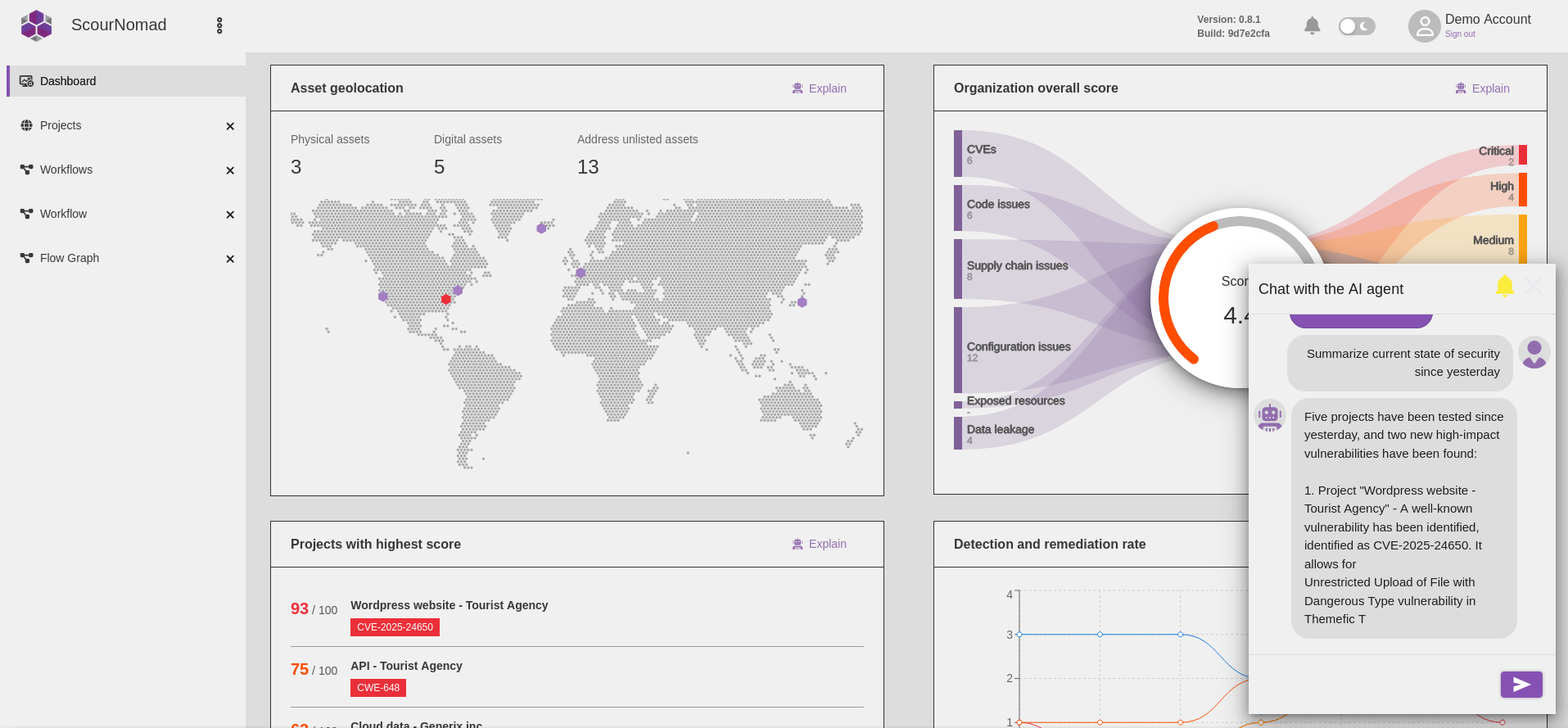
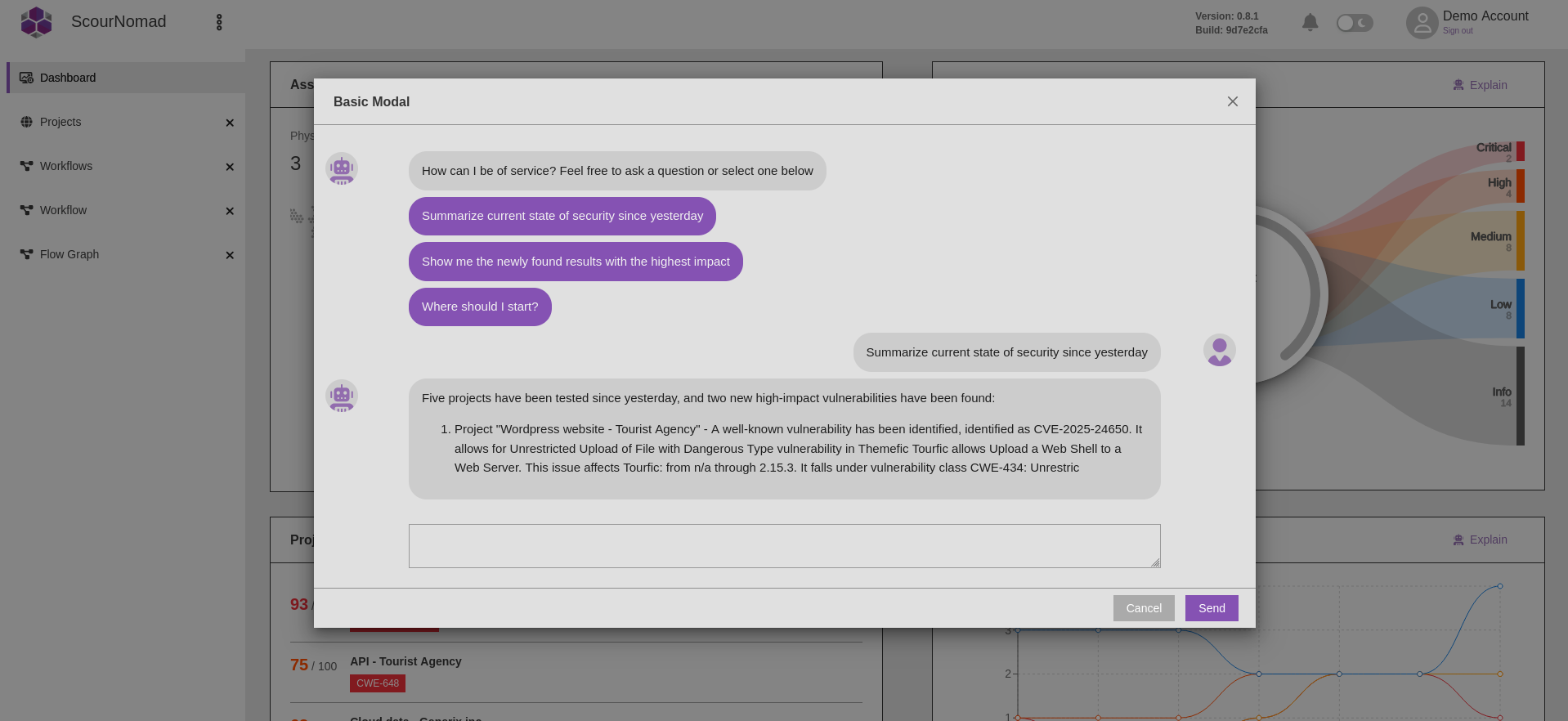
AI assistant
- Speed up remediation time using the AI assistant's help
- Validate solutions with simple retesting
- Ask the AI assistant for remediation steps and auto-fixes to further simplify the issue-solving process
- Get a complete overview of your security posture in seconds
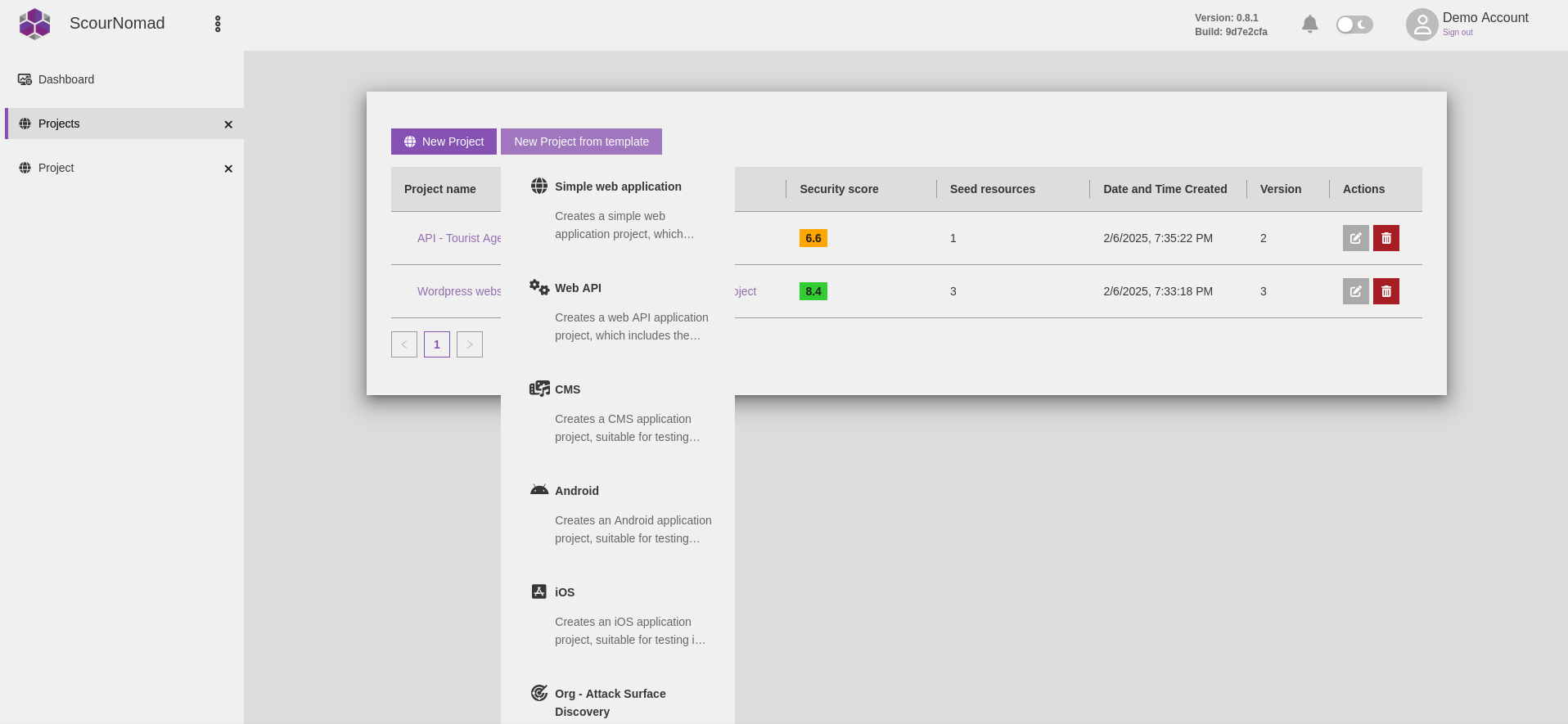
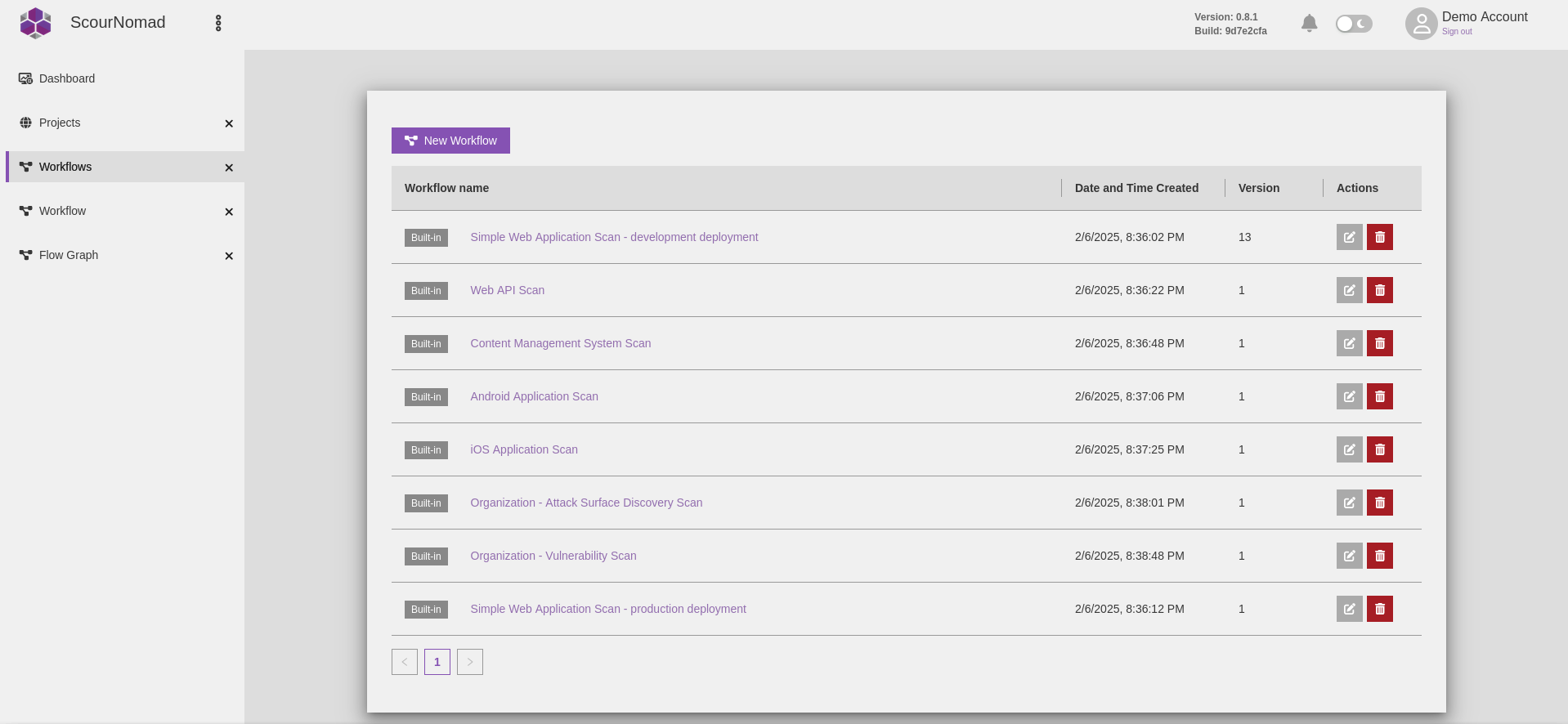
Projects and Workflows
- Simplify project setup by selecting the appropriate project template
- Select from the assortment of powerful ready-made workflows to get immediate results
- Create custom tailor-made workflows to solve your requirements
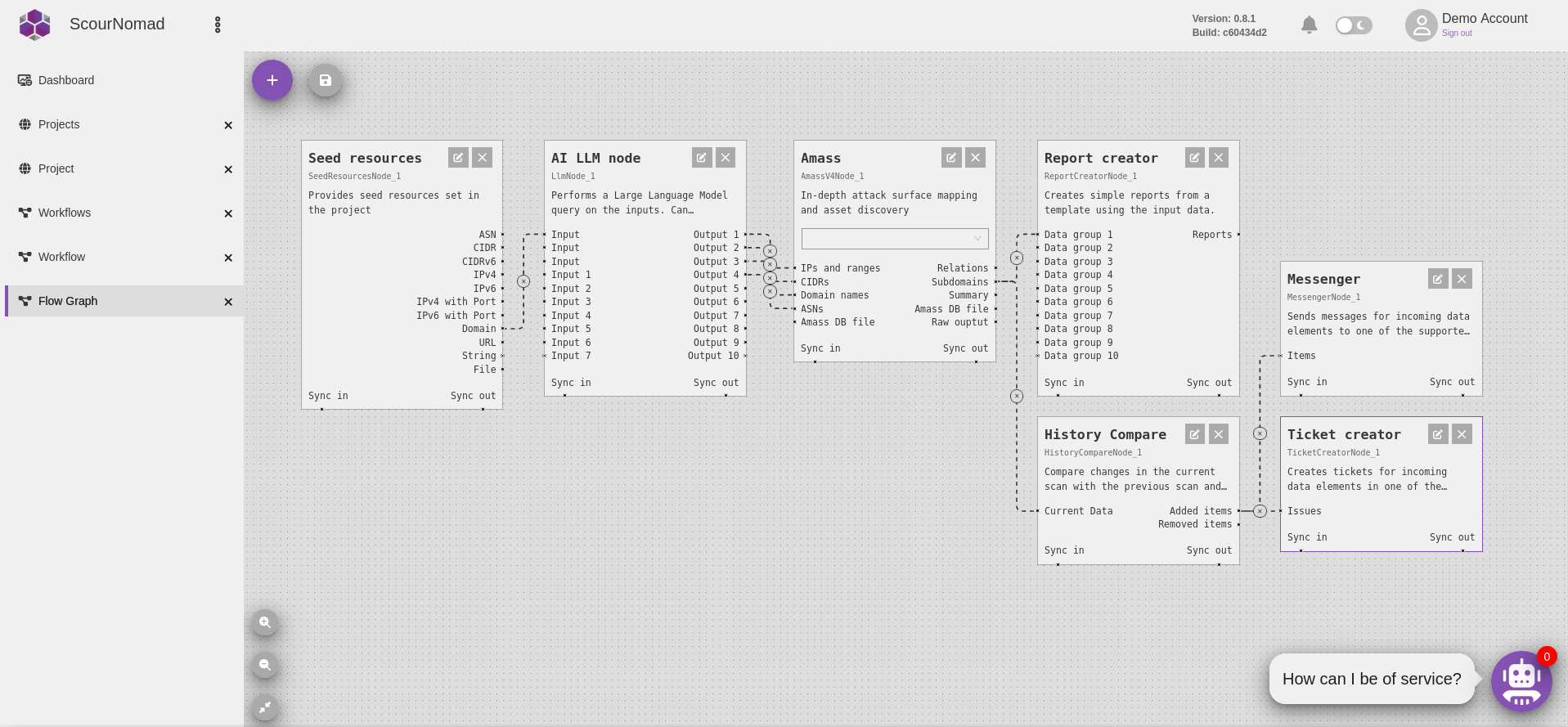
- Example on the screenshot: An AI-enhanced attack surface scanning workflow that produces results not found in traditional scans
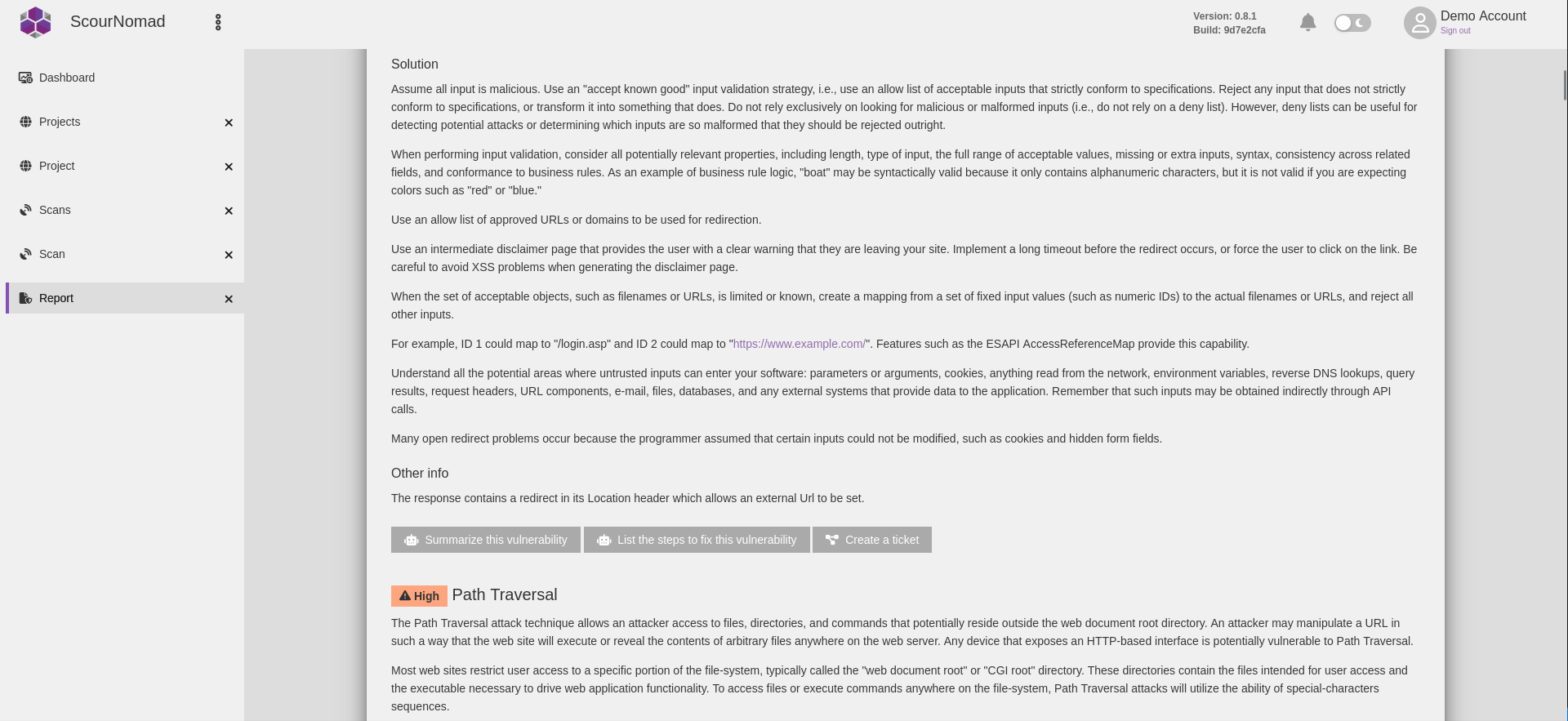
Scans and Reports
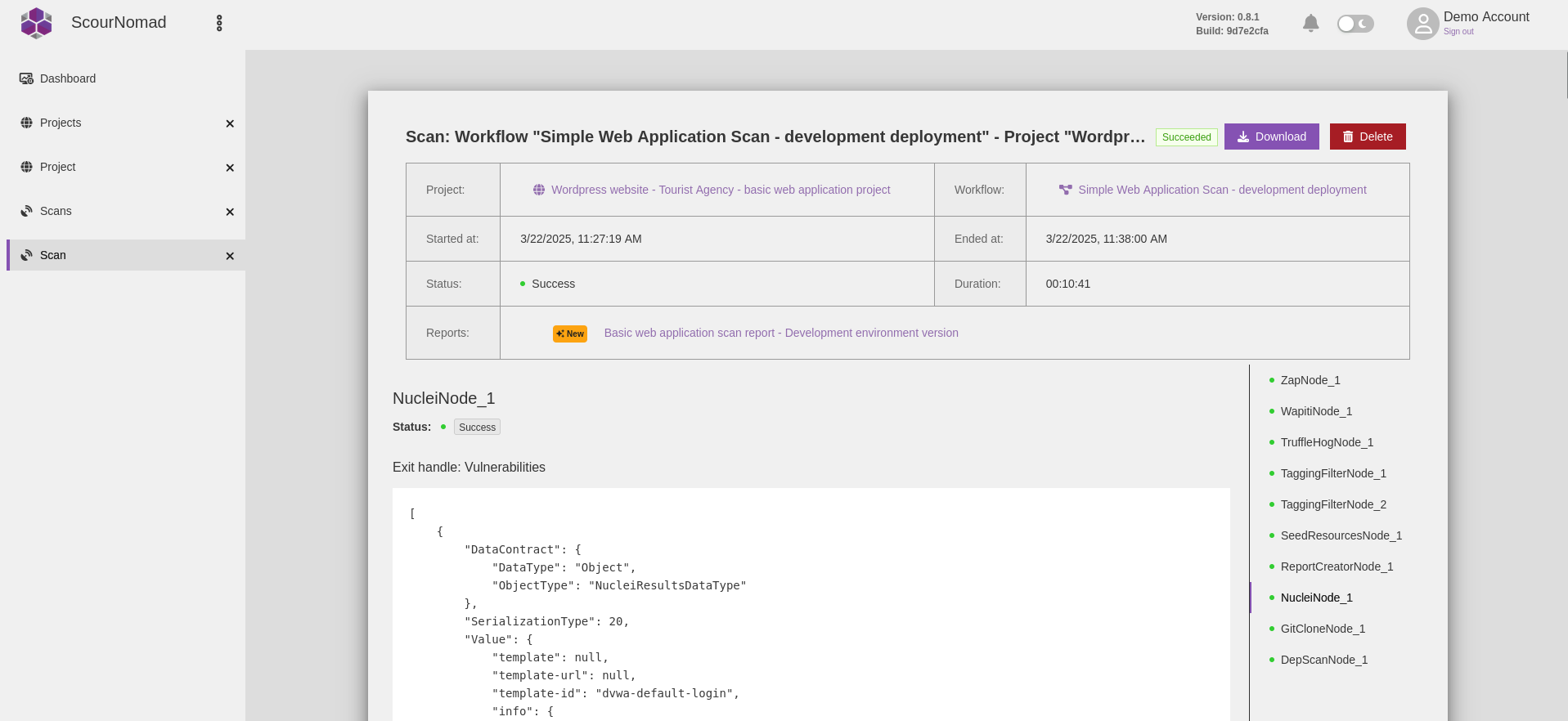
- Scans provide raw JSON-formatted results that can be passed to other tools for additional information enrichment
- Scans can produce multiple simple or complex interactive reports, which provide the capability to include manual steps
- Interactive reports can define user-triggerable actions, such as executing workflows or premade queries for the AI assistant
Ready to Transform Your Security Testing?
Schedule a 30 minute call with us to discuss how we can be of assistance - no commitment required. Our security experts will show you how ScourNomad can work for your specific needs.
- Get a 30-day free trial period for testing the fit
- Get a cost estimate without commitments